Integrating with
Integrity for 50 years
An ISO 9001 and ISO 27001-certified, trusted mission critical technology systems integrator, SIGNET has supported the complex and evolving communication, security and connectivity needs for enterprise clients for the past 50 years.









Maximizing Client Success through Personalized Solutions and Service
You require a comprehensive technology solution that enables and supports your critical business operations. As your strategic partner, we provide a single source for design, implementation and ongoing support.
- Our collaborative industry and technology experts design leading-edge enterprise systems that meet your specific needs
- Our highly-trained professional service teams work to install and integrate your enterprise system efficiently and with integrity
- Our innovative client service teams focus on delivering the highest levels of response time today, as well as the insights you need to plan for tomorrow

Who We Are
Serving all of New England, we’ve been a trusted technology provider for over four decades. Our highly-skilled industry and technology experts work to provide a superior client experience and our values inform all our interactions – with our clients, each other and our community.
What We Do
We partner with enterprise clients, across a wide array of industries to help navigate the increasingly complex technology system and infrastructure requirements in electronic security, communications, AV, IoT, and mission critical networks. With a focus on solving our client’s challenges through technology solutions, we provide holistic end-to-end services to design, install, integrate and support the complex technology environments.

Why Choose Us
Today’s enterprise systems not only need best-in-class technology, but a robust design, integration and service model to help ensure success. We take time to understand an entire technology ecosystem and identify needs and gaps – so that we can create a leading-edge solution that meets today’s requirements and helps our clients plan for tomorrow.
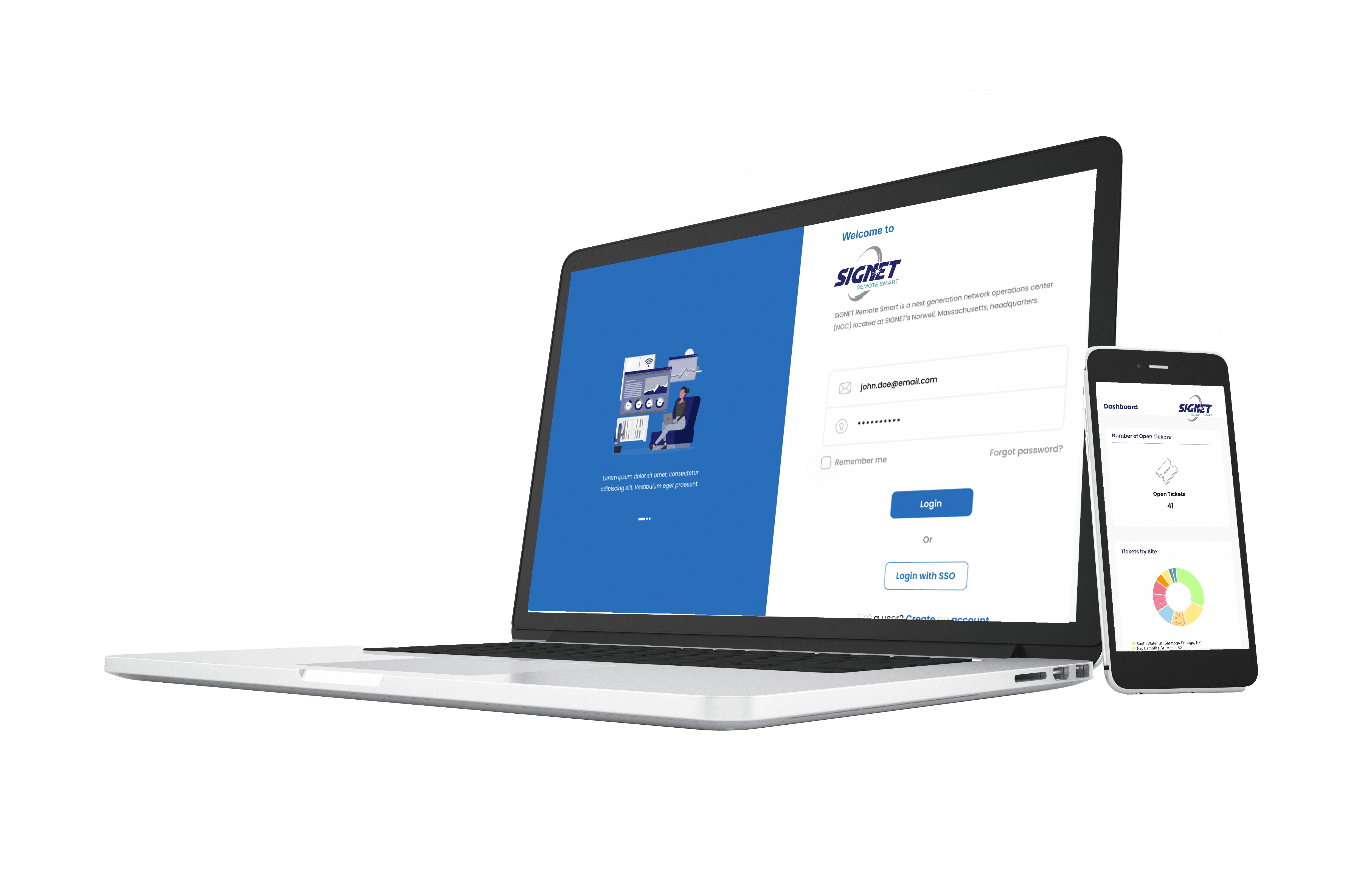
SIGNET REMOTE SMART
Client Portal & App
SIGNET clients can access support and information to help manage their critical technology systems.
- Securely initiate and manage service tickets
- Receive system notifications
- View real-time system information*
- Interact with specialized system experts*
*Requires a SIGNET Advantage plan
Fast Facts
Number of Awards
Number of Trusted Manufacturers
Industry certifications
Integrated solutions
Recent News
SIGNET Techs get good grades from UMass Police Department
After enduring a particularly challenging and lengthy purchasing experience I was delighted to have Tim Brown and Adam Cook as our installation team. They arrived punctually on Tuesday, March 12 at 6:00 am, I reviewed the scope of the project with Tim and in short...

SIGNET and Interfaith – 2023 Feed the Gala Sponsorship
Brad Caron, Barbara Caron, Steve Condon, John Tinker, Brendan Schofield and Jason Landrum were in attendance. Interfaith's “Feed the Hungry” Gala event was on December 8, 2023 at Granite Links. Interfaith Press Release: January 4, 2024 Hundreds of Supporters “Partied...

SIGNET partnered with End Hunger New England
In honor of International Volunteer Day coming up on December 5th, SIGNET partnered with the Outreach Program - End Hunger New England to package meals for those in need. The Outreach Program is a non-profit 501 (c)(3) corporation that organizes food packaging...
In the Community













